Without strong controls and security measures, your carbon accounting software could put you at risk. Data breaches can expose your strategy, give competitors an edge, and threaten your reputation, while data losses can be costly and damaging. By asking a few key questions, you can ensure your carbon accounting vendor is taking the right steps to protect your data.
Carbon accounting software ingests large volumes of data—everything from supply chain spend to procurement contracts and employee travel records. Keeping this data secure is critical, yet vendors differ widely in their security maturity, and some are still developing basic frameworks. Understanding how a company manages information security can help you avoid exposure to data breaches and losses.
Below, we break down the key security and data control features to look for when selecting a carbon accounting provider so that you can build your sustainability reporting and strategy on a foundation of trust.
Why Are Security and Data Controls Important in Carbon Accounting?
Data breaches and loss create reputational, compliance, and market risk.
If your software vendor fails to provide strong controls and security measures, they put you at risk. Data breaches can expose your strategy, give competitors an edge, and damage your reputation.
To calculate emissions, carbon accounting software handles sensitive data, including supplier pricing, contract terms, and details about procurement, manufacturing, logistics, HR-related activity, and more. This information can reveal cost structures, vendor relationships, and operational strategy—all of which most companies consider competitively confidential.
Persefoni Chief Information Officer Mike Flynn, who previously secured data and systems for the Department of Defense, emphasizes that customers’ carbon data should be handled with the utmost care—not just to avoid exposing sensitive information, but to prevent loss. “Your vendor should protect your data from the worst-case scenario,” he says. “If there’s an outage at your data center or with a critical vendor, your data should remain safe and accessible.”
Organizations often spend a great deal of time collecting, formatting, and uploading carbon data. This information allows you to assess year-over-year trends and comply with reporting obligations—and losing it can be catastrophic. If you’re right up against a reporting deadline and the servers go down, you want to make sure your software will retain as much data as possible.
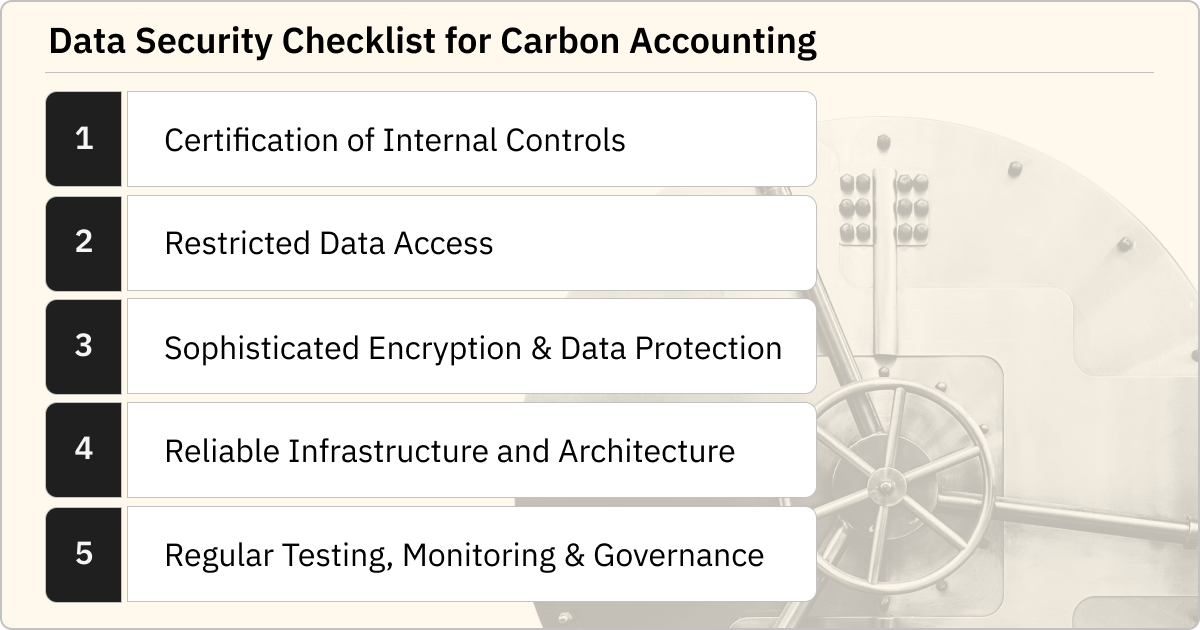
5 Critical Security Features for Carbon Accounting Software
Controls, access, encryption, infrastructure, and testing are key.
1. Certification of Internal Controls
Your vendor should conduct annual third-party audits of its security and privacy controls. It should feature SOC (System and Organization Controls) certification to verify that the right internal controls are in place to keep customer data accurate, protected, and available.
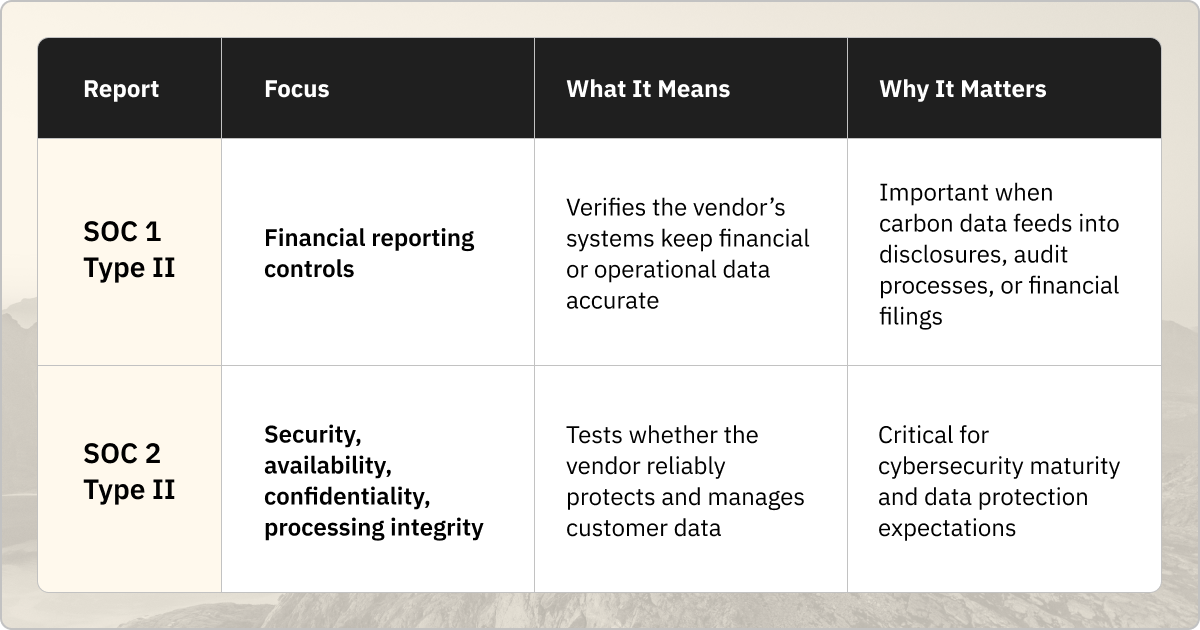
The company should provide SOC 2 Type II certification, which assures that the provider protects your data, uses repeatable security practices, and has demonstrated operational maturity. The Type II designation signifies that the controls weren’t just documented once; they were tested in practice over time. If your carbon data will be audited or tied to financial reporting, you’ll need SOC 1 Type II certification as well, which ensures that emissions calculations and financial data flows are reliable and traceable.
2. Restricted Data Access
To protect data, access should be tightly restricted and monitored. The principle of least privilege should govern access across all systems. Production access should be granted based on the role in the company, and should require a VPN and multi-factor authentication (MFA). All activity should be logged and continuously monitored for anomalies.
3. Sophisticated Encryption & Data Protection
To prevent unauthorized data access, eavesdropping, or interception, your carbon accounting vendor should provide sophisticated encryption. Look for AES-256 encryption at rest, one of the strongest methods in the industry, used by governments, banks, and healthcare systems. Your software should also offer TLS 1.2+ Perfect Forward Secrecy (PFS) for data in transit, which prevents future attackers from decrypting past data transmissions. Production data should never be used for testing or development.
4. Reliable Infrastructure and Architecture
The company’s software architecture should employ layered firewalls and network segmentation between tiers, so that even if one layer is compromised, attackers can’t easily reach sensitive data. Configurations should undergo quarterly review and enhancement to make sure they’re secure.
5. Regular Testing, Monitoring & Governance
Software vendors should conduct third-party penetration testing quarterly across network, API, and application layers, along with continuously monitoring databases, containers, and load balancers. They should have formal risk management and incident response programs in place, along with a committee that governs detection, containment, and remediation. All employees should complete annual and ongoing privacy and security training.
“We treat our customers’ data like it’s Department of Defense data.”Mike Flynn, Persefoni Chief Information Officer
Why is SOC 2 Type II Certification Important?
Certification reveals the quality of a company’s security and controls.
SOC 2 Type II is the highest level of security certification—the gold standard. It shows how a vendor protects your data, whether they have repeatable security practices, and if they demonstrate operational maturity.
It’s not enough to just confirm that a company has received SOC 2 Type II certification. You need to review the certification and see if there are any flags and which criteria the vendor has met. For example, Persefoni meets all five SOC 2 criteria: Security, Availability, Confidentiality, Processing Integrity, and Privacy.
To review a company’s SOC 2 report, follow these steps:
- Read the auditor’s opinion letter first. Look for the word “unqualified opinion” (that means it passed). “Qualified” means there were failures, and it is a red flag.
- Check the audit period (e.g., Jan 1 – Dec 31, 2025).
- Review exceptions. Any noted control failures should be discussed with the vendor.
- Confirm trust principles. Make sure they cover what matters to you (e.g., Availability for uptime-critical SaaS).
- Ask for the bridge letter if the report is older than 6 months. It confirms that nothing material has changed since.
- Never accept “SOC 2-ready” or “SOC 2 in progress” as equivalent. Those are marketing terms, not compliance.
Carbon Accounting Security Cheat Sheet: Questions to Ask Vendors
1. How do you validate your security program?
Ask whether the company has received third-party security certifications and attestations. Specifically, you should look for:
- ISO 27001: Shows that the company has security policies and controls in place and continuously improves on those systems.
- ISO 27017: Extends the ISO 27001 certification to virtual/cloud SaaS systems.
- SOC 1 Type II: Ensures integrity for financial systems.
- SOC 2 Type II: The gold standard. This is the most intensive certification, and it shows that the company operates securely on a consistent basis over time.
- ISO 42001: Standards for developing and using AI.
2. How do you validate your environment?
Ask whether the company runs network scans, and how often. They should be able to explain how they review software changes and whether they run third-party penetration tests. The results of independent scanning and testing should be published, and you should ensure that any findings have been resolved. Look for:
- SAST (code scanning)
- SCA (open source scanning)
- Container Scanning
- DAST (network vulnerability, API, and web application scanning)
- Third-party testing of the external network, application, and API
3. How do you manage data access?
The company should be able to tell you who has access to your data. Look for a vendor that heavily restricts access, including for its own staff. At Persefoni, for example, access to customer data by employees is tightly controlled—including for developers, architects, and customer success teams.
4. How much control will I have over my data?
You should retain as much control as possible over your company’s information. That means you decide who has access to data, and you can delete or export your data at any time without intervention by the vendor. Your software provider should also offer a variety of options for bulk data loading or API libraries.
5. How do you secure data in transit?
Look for TLS 1.2 encryption or higher for all data transfer—ideally, TLS 1.3. TLS 1.1 or lower is unacceptable and exposes your company. You’ll also want to make sure your vendor provides PFS (Perfect Forward Secrecy), which means that even if the security key is stolen, past communications can’t be decrypted.
6. How do you secure data at rest?
Your information should be secure when it’s stored on a database or server. The vendor should offer AES 256 encryption — you don’t want shared or hard-coded keys, and backups must be encrypted as well.
7. What’s the disaster recovery plan (and how often do you test it)?
There should be a backup plan in place in case the system goes down, whether it’s due to a malfunction or a disaster like an earthquake. Metrics to consider:
- RTO (Recover Time Objective): The length of time until service is restored (one hour is ideal)
- RPO (Recover Point Objective): How much data loss is acceptable (it should be less than 5 hours)
- Frequency of testing: The company should test its recovery at least once a year.
8. How do you manage software vendors and contractors?
Carbon Accounting SaaS providers typically rely on multiple vendors to build out their platforms. You should ensure that your provider holds its vendors and contractors to the same standards they use.
Questions you should ask:
- Is any of the development work or security outsourced or managed by subcontractors? How do you validate the people on these teams, and what access do they have?
- How often do you review vendors? Data breaches often result from vendor security issues.
9. How do you manage AI?
The company should be able to list all the AI tools it uses and their purpose.
Questions you should ask:
- Is my data used for training?
- How do I monitor what the AI is doing?
- What security programs do you have specifically for AI?

Choosing a Vendor is A Security Decision
Selecting a carbon accounting partner isn’t just about emissions methodologies and reporting features. It’s also a security and governance decision. You’re sharing thousands of critical—and sometimes sensitive—data points with your service provider. You need to know you can trust them. By asking a few vital questions upfront, you can protect your company from the reputational, security, and competitive risk that data losses and breaches create.






